All your data are belong to us
There you are, reading through your email. You notice an email that says “IMPORTANT!” so
you open it. The email tells you to open
the attachment which has a .pdf extension.
You open it, but nothing happens. You think that something
is wrong with the email, so you delete it, but you don't realize that the file was an .exe file and is working in the background to wreak havoc.
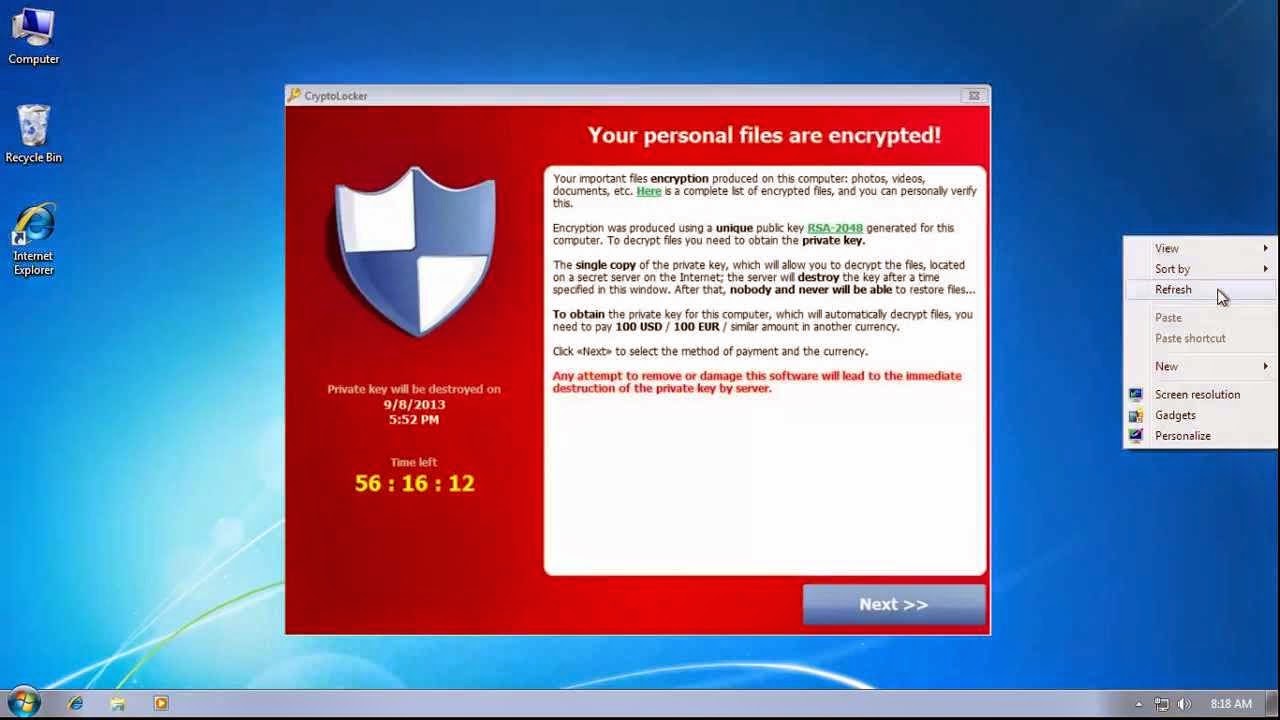
Then it happens. You see a
message box appear on your screen: “Your personal files are encrypted!”
To decrypt your files and get back your data
you must pay $300 USD. You only have a
small time window (72 hrs) to pay or you lose the ability to decrypt
forever. What do you do?
At first, you don’t believe the message. You try to find a way to close the message,
but there is none. You then try to open
a file from your computer, but you cannot.
You start thinking through; do I have a backup? Do I pay? So I know a
geek that can fix this?
Cryptolocker was introduced to the world in October of
2013. Since then hundreds-of-thousands
of computers have been infected. There
have also been many other variants of this “ransom-ware”. Some worse than others, some encrypting
files, some just denying access to your computer, all bad news. There is some good news on the Cryptolocker
front however. On June 2, 2014, the DoJ
announced that they seized the Command-and-Control (C2) infrastructure for the
botnet and shut it down, meaning that even if you get the virus, your files
will not be encrypted. Also meaning that
if you are infected and your files were encrypted, there is no way to recover
the encryption key.
While the shutdown of the C2 infrastructure for Cryptolocker
has effectively shut down the virus (for now), there are still many other
variants out there threatening to hold your data ransom for a huge profit.
So what can you do to protect your data? Below there are a few simple measures you can
take to help keep your data safe:
1. Perform Backups – Backup your data on a
regular interval based on the sensitivity of the data. If you can afford to lose a week of backups, make
sure you are backing up weekly. If you
need more current backups, then do so.
External hard drives are inexpensive and having 2 or 3 to rotate through
for backups would be a wise investment.
2. Patch your software – All software vendors offer patches for their software. Sometimes these include bug fixes, but often the patches are to fix security vulnerabilities, which viruses us to gain a foothold on your computer. Patching can prevent problems before they start. Microsoft Windows & Office, Java, Adobe, Antivirus, and other software on your computer all need to be updated in a timely manner.
3. Do not use your computer as an “administrator”
– When malware gets on your computer, it runs as the user you are logged in
as. If your user account is part of the
administrator group, the malware runs as administrator, giving it full,
unrestricted access to the machine.
Instead, run as a regular user, and setup a separate administrative user
account you use when you need to install software or change system
settings. Using User Account Control
(UAC) in Windows, you can elevate your privileges without needing to log off
and back on.
4. Do not click what you don’t know – If you
see an email from someone you do not know, or are not expecting it from, then
do not open it. If there is a link in an
email or on a website be careful before clicking it. Hovering your mouse over the link (without
clicking it!) will reveal the link location.
If it looks strange at all, do not click it. If in doubt, talk to your IT staff or someone
who is knowledgeable about these things.
For more information
see: